Как играть на деньги в казино Буй и бесплатно
Буй казино — игровое заведение нового поколения, предлагающее своим гостям ряд преимуществ. Главное из них — ассортимент игр, который постоянно обновляется самыми свежими новинками от лицензионных провайдеров. Кроме игровых автоматов, в каталоге казино также есть слоты с джекпотом, настольные игры, лотереи, видеопокер и live-игры. Лицензия, выданная правительством Кюрасао, подтверждает надежность игрового зала Буй казино и гарантирует безопасный процесс игры на официальном сайте. Удобный интерфейс, наличие фильтров для ускорения поиска автоматов, мультиязычность сайта, большой выбор валют и платежных методов обеспечивают гемблерам максимально комфортный игровой процесс.
Чтобы играть бесплатно в казино Буй не нужно регистрироваться, достаточно отыскать понравившийся слот и запустить игру в демо. Бесплатная игра позволяет изучить ассортимент Буй казино и подробнее оценить функции выбранной игры. Стоит учитывать, что демонстрационный режим есть не у всех игр. Игры из категории «Live» запускаются только на деньги, поскольку игровой процесс в них происходит в сопровождении живых дилеров из специально оборудованных студий провайдеров в режиме прямой трансляции.
Чтобы играть на деньги необходимо пройти регистрацию в Буй казино. Создание учетной записи дает игроками возможность совершать реальные ставки и выводить полученные выигрыши. Также после регистрации на сайте казино Буй игрокам открывается доступ к регулярным и индивидуальным акциям, розыгрышам, тематическим турнирам, увлекательным квестам и множеству бонусов.
Регистрация и вход в казино Буй
Регистрация на сайте подразумевает заполнение краткой анкетной формы.
Во время создания игрового аккаунта следует придумать имя пользователя и пароль, указать актуальный адрес электронной почты и выбрать валюту платежей.
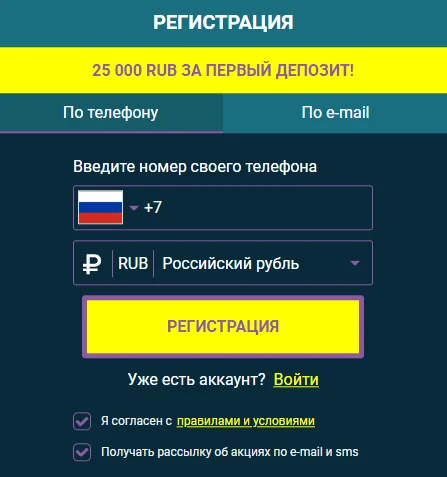
Затем для подтверждения процедуры понадобится пройти по ссылке, полученной от администрации на email.
Перед тем как зарегистрироваться, важно внимательно прочесть правила и условия работы официального сайта Буй Casino.
Главные моменты, с которыми нужно быть ознакомленным перед регистрацией в Буй Casino:
- Создавать аккаунт разрешено только пользователям в возрасте 18+ или совершеннолетним по законам страны своего проживания/пребывания, но не менее 18 лет;
- Регистрация дублирующих учетных записей запрещена;
- Лица, проживающие в странах, где азартные игры запрещены законом, не имеют права создавать игровой аккаунт;
- Регистрация сотрудников казино или его партнеров запрещается.
Бонусы в Буй
Онлайн казино Буй дает зарегистрированным игрокам большое количество дополнительных бонусных предложений. В казино существует система статусов и проводятся регулярные акции и квесты, благодаря чему времяпровождение на сайте становится более увлекательными и разнообразным. Почти все бонусы клуба Booi подлежат отыгрышу на хороших условиях. Зарегистрированные в казино Буй игроки получают:

- Приветственный пакет бонусов за пять первых внесений денег на счет;
- Персональные акции, которые обновляются каждую неделю и действуют до появления новой;
- Еженедельный кэшбек — частичный возврат проигранных за неделю средств;
- Статусы игроков — чем выше статус, тем более выгодные условия для игры получает пользователь.
Стартовый бонус предполагает 5 подарков за первые 5 депозитов для новых игроков. Каждый бонус необходимо активировать в личном кабинете перед пополнением счета. В рамках данного предложения игроки получают:
- За первый депозит от $20 — бонус 200% до $300 на бонусный баланс;
- За второе пополнение от $15 — 50 фриспинов;
- За третий депозит от $15 — 25 фриспинов;
- За четвертый от $15 — 50 фриспинов;
- За пятое пополнение от $20 — 50% до $300 на бонусный счет.
Каждый игрок, который хотя бы раз вносил деньги на депозит, получает персональные акции. Они обновляются раз в неделю в личном кабинете и действуют до появления новой. Такие акции проводятся с учетом предпочтений конкретного пользователя и позволяют получать больше призов, знакомиться с провайдерами и новыми азартными играми.
Кэшбэк в казино Буй начисляется всем игрокам, которые играют на реальные деньги. Он подразумевает частичный возврат средств от проигранной за неделю суммы. Высчитывается по формуле: сумма пополнений за 7 дней – сумма выводов за эти же 7 дней – остаток на счету на момент расчета кэшбэка. Он начисляется автоматически реальными деньгами на основной счет и является единственным бонусом, который не требует отыгрыша. Точный процент возврата зависит от статуса: Wooden Lemur — 4%, Silver Eagle и Golden Alligator — 5%, Platinum Elephant — 6% и Diamond Lion — 7%.
Статусы игроков в Буй разделены на 5 уровней. Чем выше статус, тем больше процент кэшбэка, больше лимит на вывод средств в сутки и выгоднее условия акций. Игрокам с наивысшим статусом присваивается персональный менеджер. Статусы обновляются ежедневно и зависят от суммы депозитов за прошедший месяц.
- Wooden Lemur — менее $250;
- Silver Eagle — $250;
- Golden Alligator — $1 000;
- Platinum Elephant — $5 000;
- Diamond Lion — $10 000.
Вывод денег и техподдержка
Онлайн-казино Буй — безопасное азартное заведение с быстрыми выплатами. Срок вывода для игроков с подтвержденным аккаунтом здесь обычно не превышает четыре часа с момента размещения заявки на вывод. Для верификации учетной записи необходимо отправить в службу техподдержки скан или фото документа, подтверждающего личность. Для быстрого вывода важно использовать платежную систему, через которую был внесен депозит.
Пополнить баланс на сайте казино можно минимум на $5, а для вывода доступно минимум $10. Максимальный лимит на снятие средств в сутки для игроков в статусе Wooden Lemur, Silver Eagle и Golden Alligator равен $3000, Platinum Elephant — $5000, Diamond Lion — $7500. В казино предусмотрено более десяти популярных платежных систем, что обеспечивает игрокам максимальное удобство и безопасность пополнения счета и снятия денег с него. Среди них – карты Maestro, Visa, Mastercard, Система быстрых платежей, Neteller, Perfect Money, WebMoney, Rapid Transfer, MuchBetter, Piastrix, Skrill, Astropay, Binance Pay и криптовалютные кошельки.
Служба технической поддержки азартного клуба Буй казино помогает игрокам решить все сложности, связанные с игрой на сайте — регистрация, перевод платежей, поиск работающего зеркала Booi, начисление и отыгрыш бонусов и т.д. Онлайн помощь доступна без перерывов и выходных. Обратиться к менеджерам есть возможность написав на электронный адрес или в лайв-чат, встроенный на сайте.





